By: FIDO staff
The first two days of Authenticate 2025 delivered strong technical content, user insights and lots of thoughtful discussions.
The final day of Authenticate 2025 went a step further taking attendees on a deep dive into really important current and emerging topics for authentication including biometrics, agentic AI and verifiable credentials.
Passkeys and Verifiable Digital Credentials are Not Competitors
A key theme across multiple sessions at Authenticate 2025 was the growing need and development of standards for Verifiable Digital Credentials.
In a session led by Christine Owen, Field CTO at 1Kosmos and Teresa Wu, Vice President, Smart Credentials & Access at IDEMIA Public Security, the roles of passkeys and verifiable digital credentials (VDCs) within the evolving landscape of secure digital identity were clarified.
They emphasized that passkeys and VDCs are not competing technologies. Instead, they are best used together to strengthen both authentication and identity verification processes. Passkeys offer privacy preservation and are resistant to phishing, while VDCs provide digital representations of identity attributes that can be selectively shared when needed.
Breaking Glass: Restoring Access After a Disaster
In a thought-provoking session, Dean H. Saxe, Principal Security Engineer, Identity & Access Management at Remitly, explored the challenges and importance of digital estate management, particularly in the context of disasters and emergencies.

Saxe described how personal experiences and recent natural catastrophes highlight the necessity of preparing for sudden loss of access to digital assets.
A hands-on experiment conducted by Saxe tested how well a “break glass” process works when all personal devices are lost. The process included relying on physical identity documents and a safe deposit box to regain access to important accounts like 1Password, Apple iCloud, and Google services. Saxe faced unexpected obstacles, such as a missing credential and issues getting recovery codes, which illustrated the real-world difficulties of these situations.
The findings of Saxe’s experiment stressed the need for regular testing and updating of disaster preparedness plans.
“So the failure to test your backup strategy means that you do not have a valid backup strategy,” Saxe said.
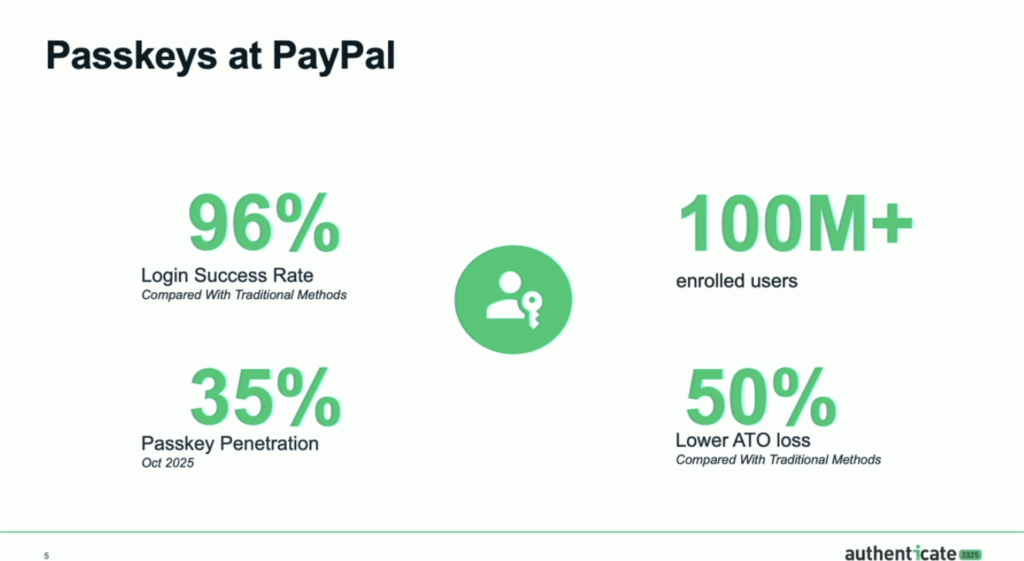
From the Trenches: Passkeys at PayPal
PayPal is an early adopter of passkeys with the initial motivation being focused on reducing password reliance.
“It’s time to break free from the password prison,” Mahendar Madhavan, Director of Product, Identity at PayPal said.
PayPal launched passkeys in 2022, saw a surge in mid-2024, and now boasts more than 100 million enrolled users with a 96% login success rate. This surge has delivered results—phishing-related losses have dropped by nearly half compared to traditional password and OTP methods.
Mohit Ganotra, Identity PM Lead at PayPal explained that initial efforts zeroed in on user education and reducing friction during login. By optimizing the login experience and targeting enrollment prompts during checkouts and password recovery, PayPal now sees 300,000 incremental enrolments each month from checkout alone, plus 75,000 from automatic passkey upgrades.
“Passkeys is still a new technology, it needs to go through the adoption curve that every new technology has,” Madhavan said. “So you as a relying party need to nudge users, guide users, encourage users to adopt a passkey at various points in their journey and how you do it is, you hyper personalize the content for consumers and users, and you talk in their language.”
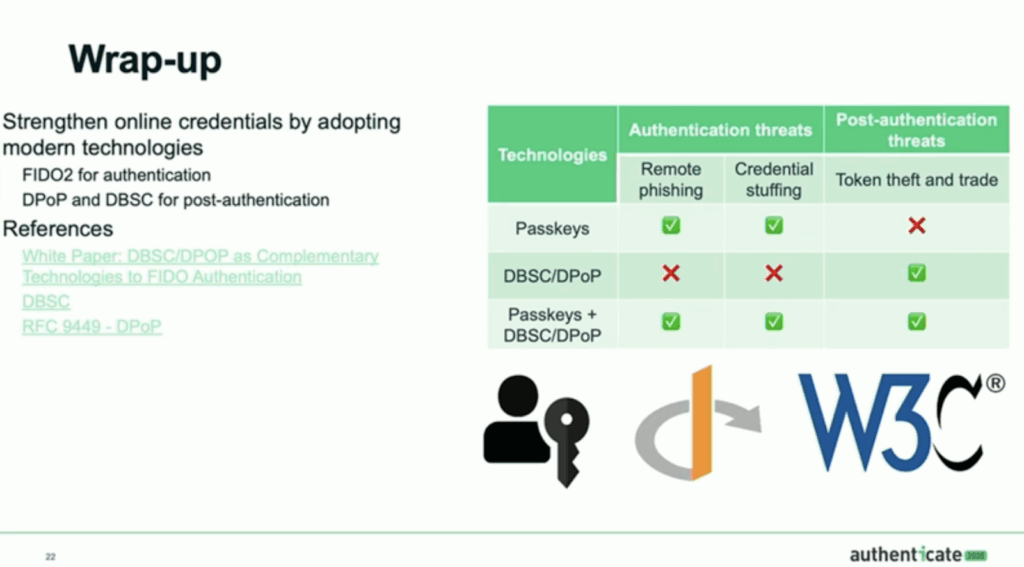
Safeguarding Enterprise Online Credentials Post Authentication
While passkeys solve authentication security, post-authentication remains vulnerable through bearer token theft and session hijacking.
There are however numerous technical approaches that can help mitigate the risk, which were described in detail by An Ho, Software Solution Architect at IBM and Shane Weeden, Senior Technical Staff Member at IBM.
The session introduced two complementary technologies designed to address this vulnerability. DPoP (Demonstrating Proof of Possession) extends OAuth 2.0 to create sender-constrained access and refresh tokens for API flows, while DBSC (Device-Bound Session Credentials) binds browser session cookies to specific devices. Both technologies use asymmetric cryptography to ensure that stolen credentials become unusable by attackers, as they require proof of possession of private keys that only the legitimate client or browser holds.
“We believe that you need to look at a holistic view of your sessions,” Weeden said. “You need to look at not just how clients and users log in, but also how to maintain a form of continuous authentication with the client or browser that is utilizing that session.”
From the Trenches: Improving Experience and Security at Databricks with Passkeys
Meir Wahnon, Co Founder of Descope, explored how Databricks approached the challenges of unifying authentication and improving security across multiple cloud-based apps.

Databricks partnered with Wahnon’s company to figure out the best approach. The fragmented login experience had made it hard for users and the IAM team to manage access and maintain full visibility. Databricks tackled this by adopting a centralized identity provider and federation to ensure a more seamless single sign-on process. A major focus was the decision to add passkeys as an optional multi-factor authentication method. This choice was driven by Databricks’ commitment to balancing strong security for customers with a smooth, low-friction user experience.
The deployment of passkeys came with careful attention to user adoption and support. Databricks made passkeys optional to minimize disruption, and included easy rollback options if customer uptake became a challenge.
“The balance between user experience and security is always a question when you build a user journey,” Wahnon said.
From the Trenches: Alibaba’s Passkey Story
Alibaba is expanding its use of passkey authentication across business units including AliExpress and DingTalk.
Preeti Ohri Khemani, Senior Director at Infineon Technologies which works with Alibaba explained that the main goal was to improve security and user experience by reducing dependence on traditional passwords and costly SMS one-time passwords. The rollout has led to faster, more convenient logins and a smoother registration process for users.
On AliExpress, the deployment of passkeys simplified the login flow and eliminated extra steps for users. This change resulted in a reported 94% increase in login success rates along with an 85% reduction in login times. Users no longer need to manage passwords or wait for verification codes, which also lowered operational costs and security risks.
DingTalk, Alibaba’s internal messaging platform with 28 million daily active users, has similarly benefited from passkey integration. Engineers at Alibaba focused on making passkey adoption easy by sharing clear coding samples, open-source libraries, and helpful tools.
Keynotes: The Path to Digital Trust

Ashish Jain, CTO of OneSpan used his keynote to explore the ongoing challenge of establishing trust in digital interactions. Jain traced the journey from physical trust in face-to-face transactions to today’s anonymous digital world.
Ashish outlined the tension between user experience and security. He cited how complex password policies and frequent multi-factor authentication can frustrate users, yet they are essential for protection. The discussion highlighted how the industry is coming closer to a practical solution through the adoption of passkeys.
“In the physical world, trust is emotional,” Jain said. “In the digital world, trust is an architecture.”
Keynote: Biometrics Underpinning the Future of Digital Identity
Continuing on many of the same themes from Amlani’s keynote, Stephanie Shuckers, Director, Center for Identification Technology Research (CITeR), University of North Carolina – Charlotte and Gordon Thomas, Sr. Director, Product Management, Qualcomm provided more insights on the critical nature of biometrics.
Thomas noted that while face recognition remains popular, fingerprints offer enhanced privacy because they are less likely to be exposed online or through surveillance.
“It’s not really about proving who you are, but it’s about building and securing your digital identity layer by layer with trust every time you use it,” Thomas said.
Shuckers noted that there is a need for strong assurance levels in biometric technology on consumer devices. That’s where standards help ensure both user safety and usability. The FIDO Alliance’s programs test biometric systems for vulnerabilities such as deep fakes and injection attacks. These certifications are crucial for building trust in digital identity systems.
Keynote: Microsoft Details What’s Needed to Authenticate Agentic AI
Pamela Dingle, Director of Identity Standards, Microsoft led a session on the challenges and opportunities in authenticating AI agents within enterprises.
She stressed the importance of understanding what an agent is and pointed out that simply asking “who authenticates the agent” is not enough. Dingle highlighted the complexity that arises from having many agents running in different domains, each with unique tasks and identifiers. Administrators often struggle to see the full chain of actions, which complicates decision making and resource management.

Dingle introduced the idea of using “blueprints” and “task masters” to authenticate not just the agent but also the context and source of its tasks. She emphasized that knowing only the identifier is not enough. The future will require richer, composite data about each agent’s purpose and origin.
“The agentic AI push gives us an opportunity to build the tools enterprises need to run better.”
Keynote Panel: Digital Wallets and Verifiable Credentials: Defining What’s Next
Verifiable credentials was a hot topic at Authenticate 2025 and it was one that was tackled in the final keynote panel.
The panel included Teresa Wu, Vice President, Smart Credentials and Access at IDEMIA Public Security, Loffie Jordaan, Business Solutions Architect at AAMVA, Christopher Goh, International Advisor, Digital Identity & Verifiable Credentials at Valid8 and Lee Campbell, Identity and Authentication Lead, Android at Google.
The discussion began with an overview of the ecosystem, emphasizing the interaction between the wallet, issuer, and relying party. This “triangle of trust” serves as the cornerstone for secure digital credential use. Panelists stressed the need for privacy, interoperability, and certification as this shift accelerates, highlighting lessons learned and ongoing challenges like fragmentation across platforms.
FIDO Alliance’s growing focus on digital credentials was described as a catalyst for industry progress. “FIDO is getting involved in the digital credential space,” Campbell said. “FIDO does an exceptional job at execution.”

That’s a Wrap!
Wrapping up the Authenticate 2025 program, FIDO Alliance Executive Director Andrew Shikiar emphasized that the event continues to grow year by years.
For the 2025 event there were 150 sessions and 170 speakers.
“Passkeys are driving measurable business outcomes,” Shikiar said. “One thing I thought was really cool this year about some of the presentations, it wasn’t just another ‘rah rah’ passkeys are great story, but also companies are coming back for their second time or third time, talking about progress and lessons learned and how they’re evolving, pivoting and growing.”
Speaking of growth, the Authenticate event is growing for 2026, with a new Authenticate APAC event set for June 2-3 in Singapore. Authenticate 2026 will be back in California at the same time next year.
Between now and then, the FIDO Alliance will be sharing lots of informative content and hosting educational events. Stay connected and sign up for updates.

